Organizational Training Challenges Today
Evolving cybersecurity threats requires an agile and adept workforce. Defending the network requires hands-on training of complex hardware, software, and network configurations.
When testing and evaluating new software or hardware, providing timely and accurate information to decision makers and program managers is the ultimate objective.
Syndicus NACON is proud to have been recently approved as a Licensed Training Provider (LTP) for the Cybersecurity Maturity Model Certification (CMMC) Accreditation Board. Using our VirtualOnDemand Learning Management System and cyber range, our platform offers higher knowledge and skills retention with hands-on exercises.

VirtualOnDemand®
VirtualOnDemand is a powerful and highly scalable cyber range engineered to enhance cybersecurity training and testing and evaluation programs.
By using our VirtualOnDemand training platform, our clients realize reduced training costs and IT resource needs. VirtualOnDemand requires only an Internet connection and modern browser.
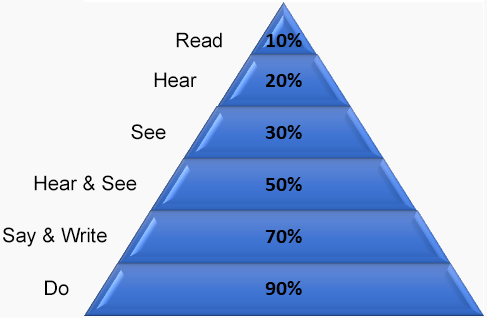
National Training Laboratories, Bethel Maine. Also – 1954, Audio-Visual Methods in Teaching, Edgar Dale Dryden Press, New York
VirtualOnDemand is skills-based, so users can maximize their experience in the shortest time.
Bottom line: Higher knowledge and skills retention with Hands On Exercises.
Integration with LMS
The cyber range is bundled with a Learning Management System (LMS) but use of our LMS is optional. The cyber range can integrate with existing Learning Management Systems and ships with an API to integrate into any web-based training platform.
Licensed Partner Publishers (LPPs) working with Syndicus NACON are assigned a private development portal where content can be staged directly in the LMS. The LPP retains their intellectual property and can use the cyber range to provide hands-on exercises.
Security
VirtualOnDemand isolates the training environment to protect production resources. Malware, applications, and devices are isolated in a private cloud from production environments, while having the ability to interact with them.
The virtualized environment does not require special permissions, is separated physically and logically from networks, and can be accessed and fully controlled from both Government Furnished Equipment (GFE) and personal computers without requiring any special security concessions.
Accreditation
VirtualOnDemand deployments have been accredited under the Risk Management Framework (RMF) and have been deployed in classified environments.
More
Collaboration Tools – Shoulder Surfing allows instructors to view and interact with a student’s virtual machine. Instructor Sharing allows instructors to broadcast their virtual machines to students for demonstration purposes.
Scenario Builder – An easy-to-use interface for creating virtual machines and complex networks.
Automated Housekeeping – Automatic, unattended provisioning and booting of the virtual machines, followed by reallocation of the virtual machines back into the resource pool upon completion.
Persistence – Users can save an instance of the network so it can be accessed later.
Performance-based Scoring Platform – Instructors can monitor student activity in the network in real-time to assess the completion of training objectives.
Syndicus NACON and Logical Operations to Launch Cybersecurity Recruiting Center of Excellence
FOR IMMEDIATE RELEASE: Rochester, New York – February 2, 2022 – Syndicus NACON and Logical Operations have announced a strategic partnership to create a cybersecurity training and placement program called Cybersecurity Recruiting Center of Excellence [...]
Syndicus NACON Offering Free Webinar: Matching Cybersecurity Skills to Jobs, A Step to Bridge the Skills Gap
As part of our partnership with CertNexus, Syndicus NACON will be offering a free webinar entitled "Matching Cybersecurity Skills to Jobs, A Step to Bridge the Skills Gap".
Will the “Real” CMMC Consultant Please Stand Up?
Let's face it, the skill and experience level required to become a registered practitioner (RP) and hang your registered provider organization (RPO) shingle on, is not a big leap from, say, an entry level IT role.


